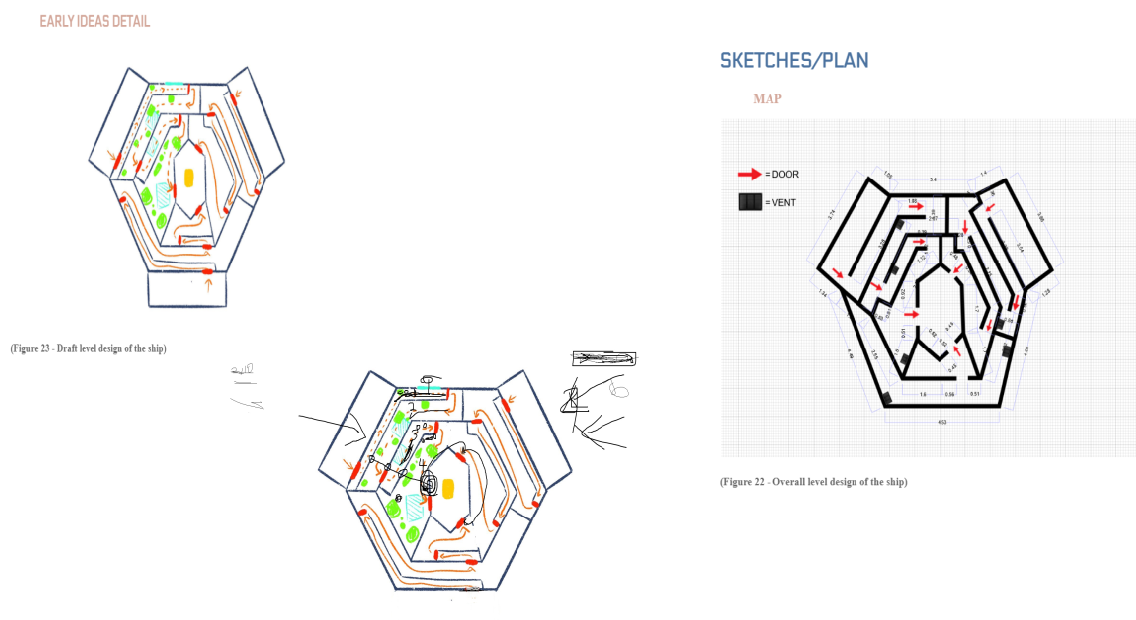
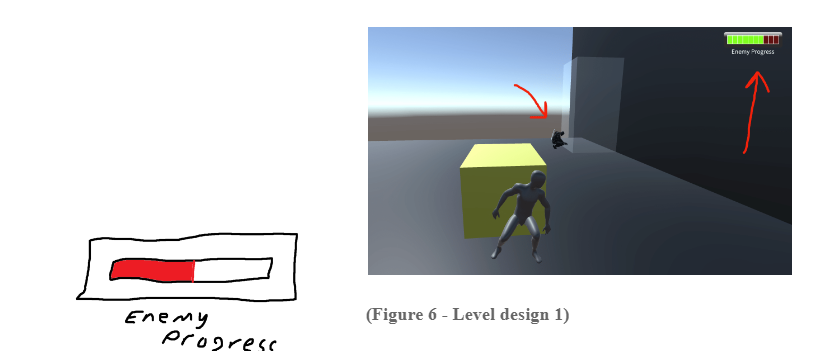
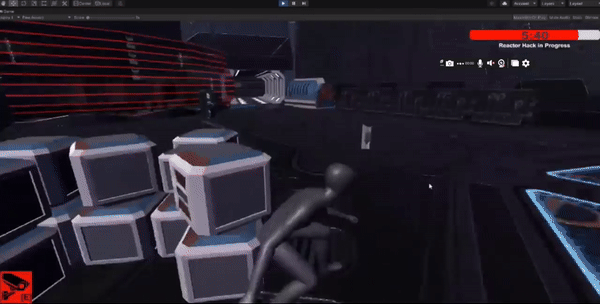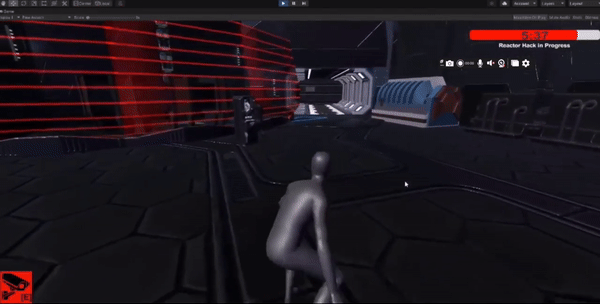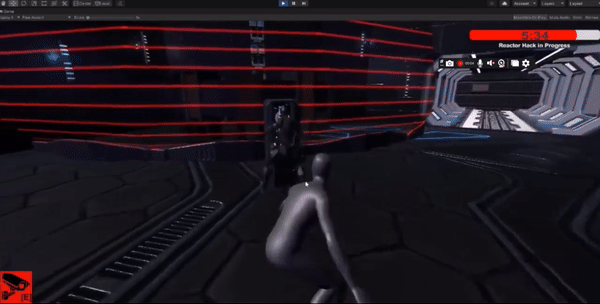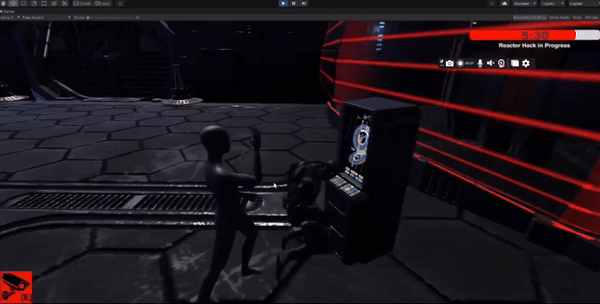
Core Game Mechanics
This section outlines the core mechanics of the game I specifically worked on.
Feature 1 - Timer Design
Conceptualization:
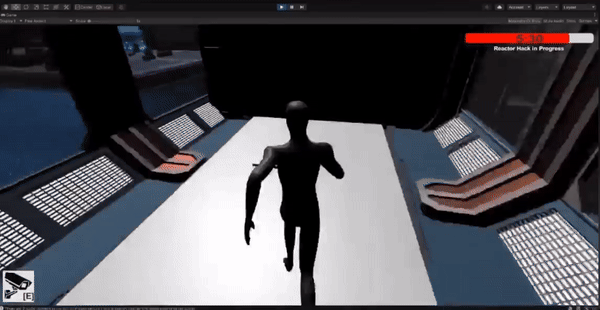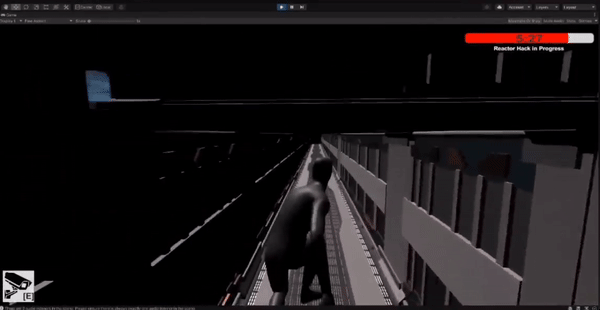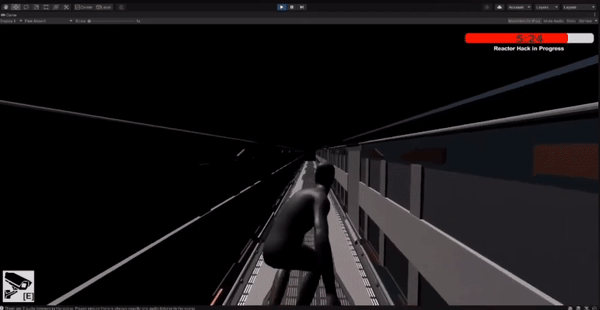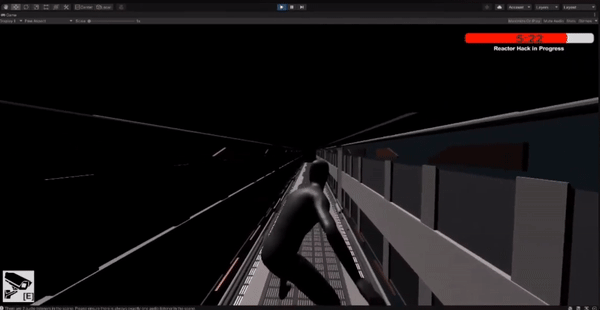
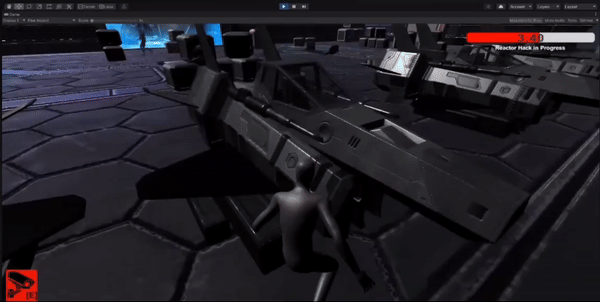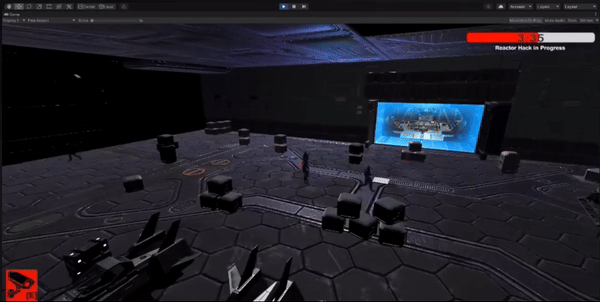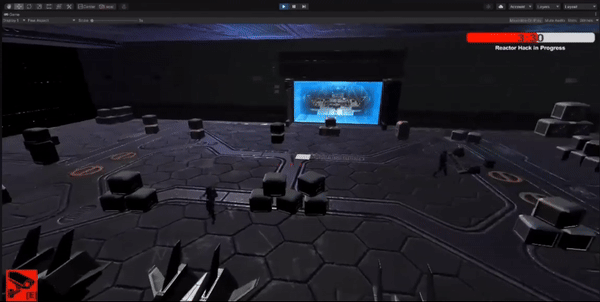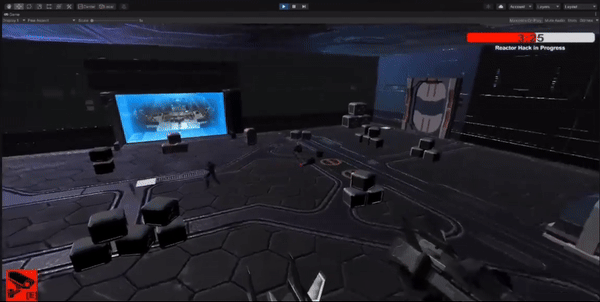
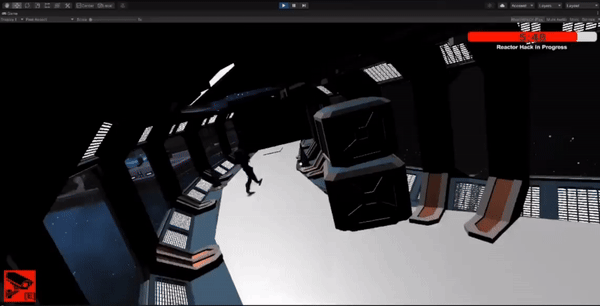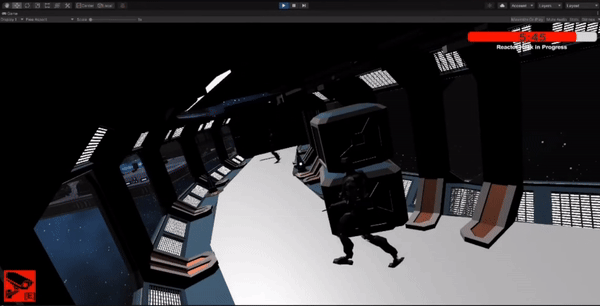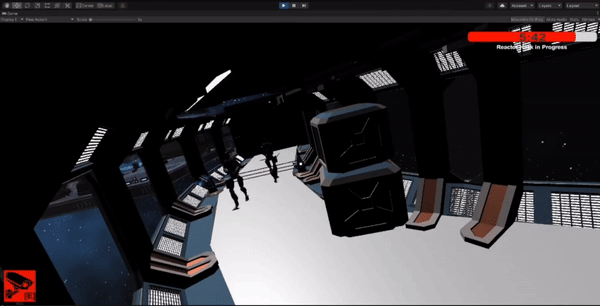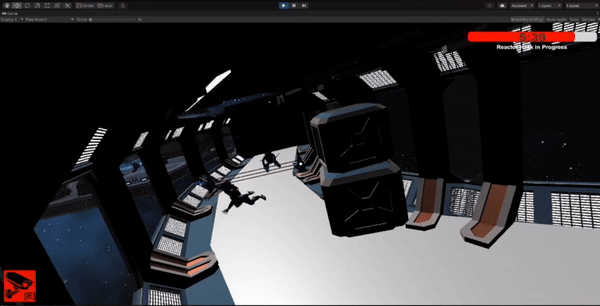
The player has a limited time to stop enemies from hacking the main shipping area.
Implementation:
Implemented a timer mechanic where the player needs to reach the hacking area within a specific time limit.
Testing and Iteration:
Tested and iterated on the timer system to ensure balanced gameplay and appropriate difficulty level.
Feature 2 - Stealth Design
Conceptualization:
Designed stealth mechanics where the player can hide behind obstacles and use vents for navigation.
Implementation:
Implemented crouching, hiding, and vent crawling mechanics to enhance stealth gameplay.
Testing and Iteration:
Tested and refined stealth mechanics to ensure smooth player experience and balanced difficulty.
Feature 3 - Hacking
Conceptualization:
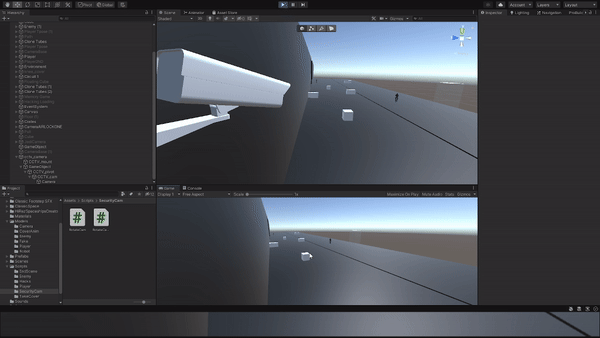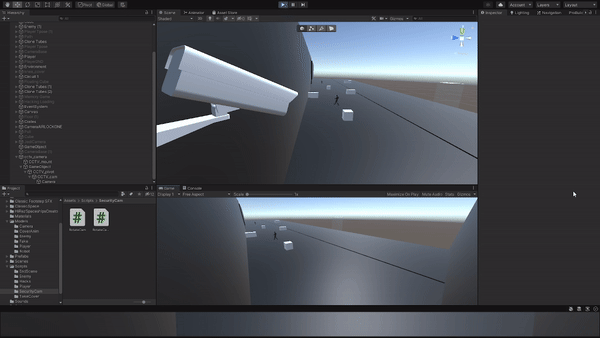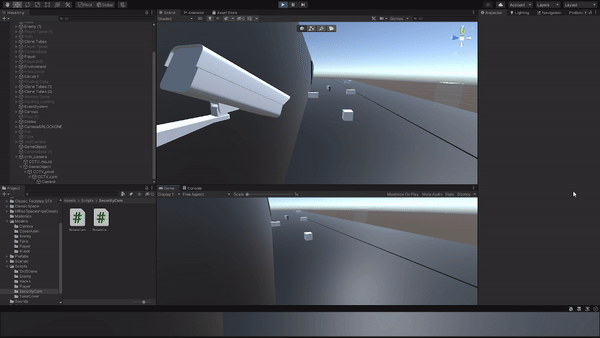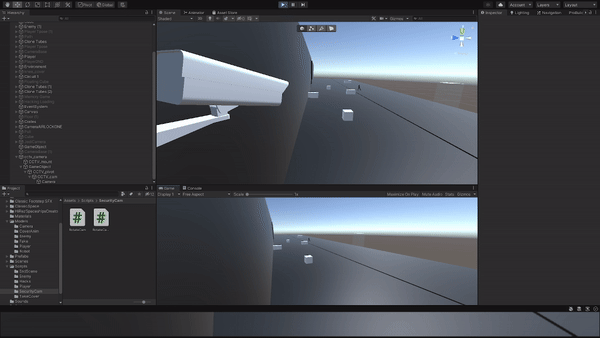
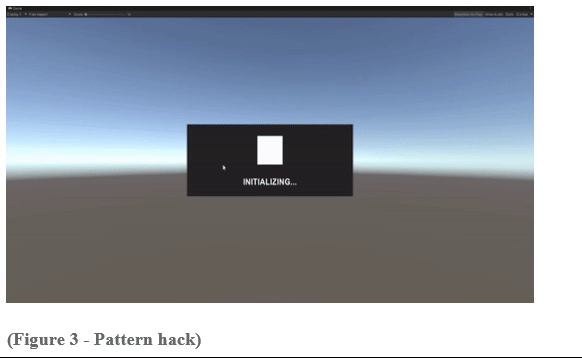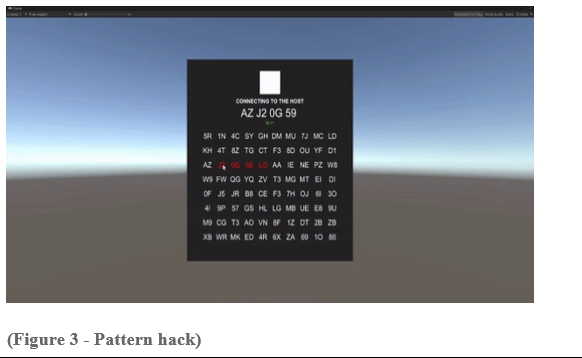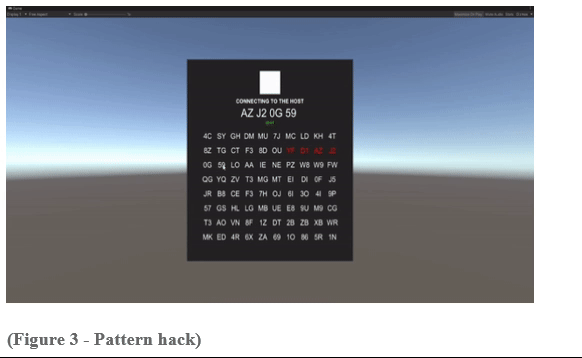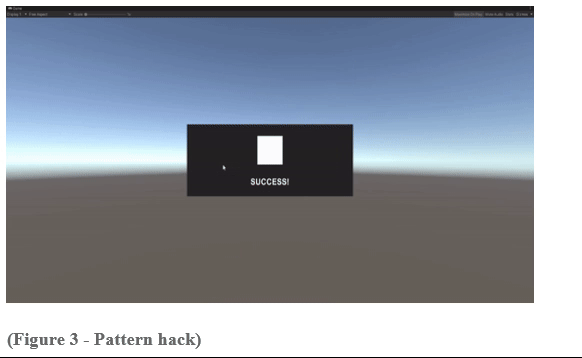
Designed a hacking mechanic where the player can remotely access cameras to gather information.
Implementation:
Implemented a hacking interface and proximity-based camera interaction system.
Testing and Iteration:
Tested and adjusted hacking mechanics for usability and effectiveness in gathering intel. Additionally, incorporated camera proximity mechanics to require the player to be in close range for camera hacking.
Feature 4 - Electric Fences and Camera Defense
Conceptualization:
Designed areas with electric fences and cameras equipped with defensive capabilities to enhance player challenge and strategy.
Implementation:
Implemented electric fences as environmental hazards and cameras with shooting lasers to stun enemies.
Testing and Iteration:
Tested electric fence mechanics for player interaction and camera defense effectiveness in deterring enemy movement. Iteratively refined mechanics to balance challenge and player experience.
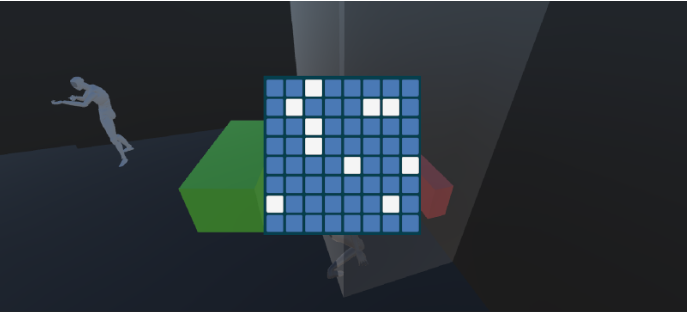
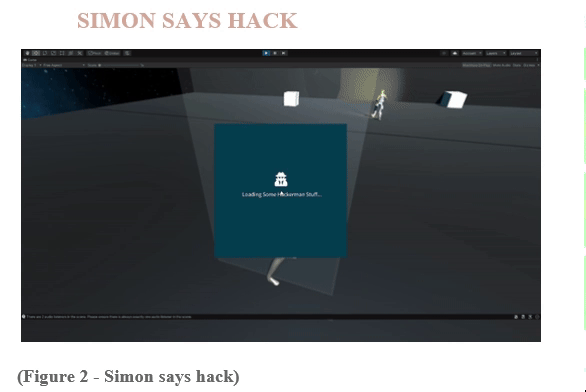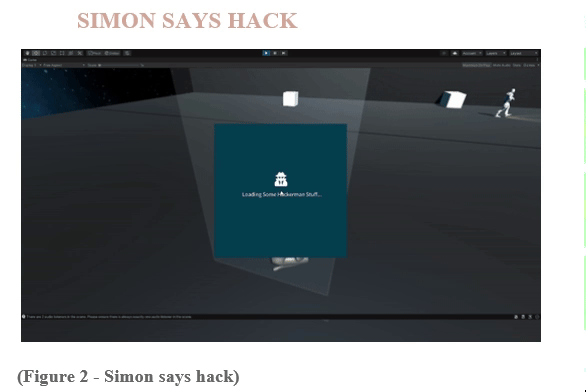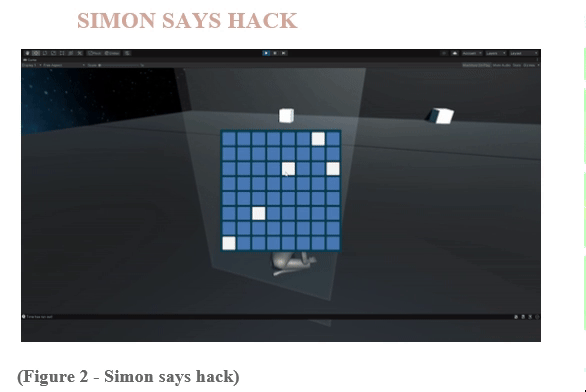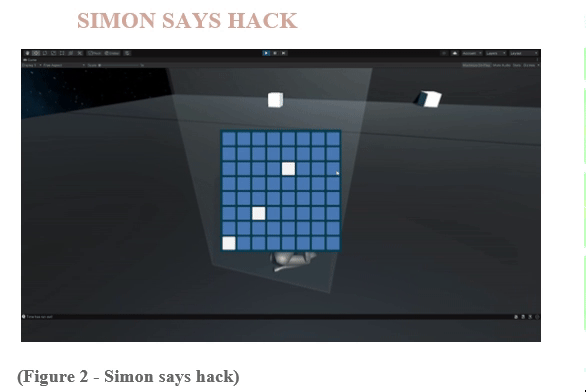
Feature 5 - Hacking: Simon Says Hack
Conceptualization:
Designed a hacking minigame where the player must remember and mimic a sequence of button presses.
Implementation:
Implemented a Simon Says-style hacking minigame with increasing difficulty levels.
Testing and Iteration:
Tested and adjusted the Simon Says Hack minigame to ensure it provides a challenging yet enjoyable experience.